What is Zero-day Defense?
eScan's Zero-day Defense is a proactive security system designed to detect and block previously unknown threats—those that exploit vulnerabilities for which no patch exists and no signature has been developed. Unlike reactive security solutions that depend on prior knowledge of threats, our system analyzes behaviors, patterns, and activities to identify malicious intent before damage occurs.
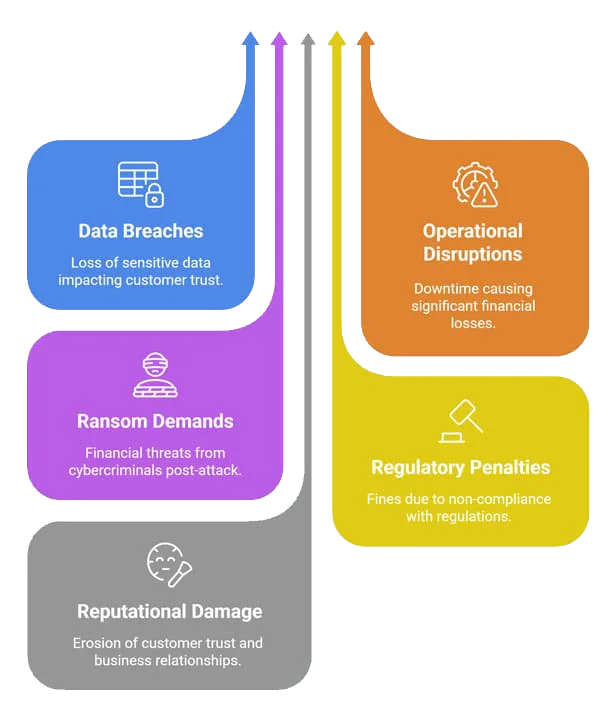
The term "zero-day" refers to the fact that developers have had zero days to address and patch the vulnerability being exploited. These threats represent some of the most dangerous cybersecurity challenges because they target undiscovered vulnerabilities, giving organizations no time to develop and implement protective measures through conventional means.