What is Workspace Tenant Control?
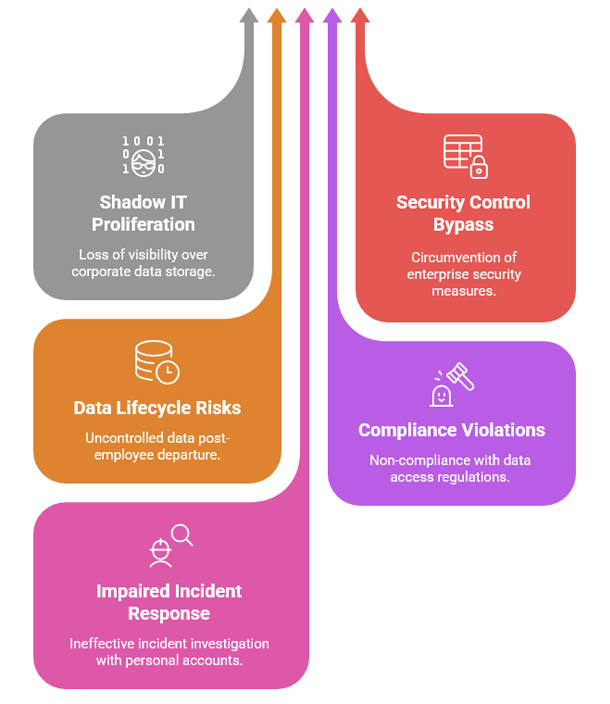
Workspace Tenant Control is an advanced security feature within eScan Enterprise DLP that enables organizations to implement and enforce strict access controls for cloud-hosted services. By creating boundaries around which accounts can access corporate resources, this technology prevents unauthorized data access, improves visibility, and strengthens your overall security posture.
The technology works by identifying and controlling access based on domain credentials or tenant IDs-the unique identifiers associated with your organization's cloud subscriptions. When an employee attempts to access a cloud service, eScan verifies that they're using corporate credentials rather than personal accounts, preventing potential security policy violations and data leakage vectors.
Unlike basic access control systems that simply block entire services, Workspace Tenant Control allows productive use of essential cloud tools while ensuring they're accessed only through secure, monitored corporate channels.